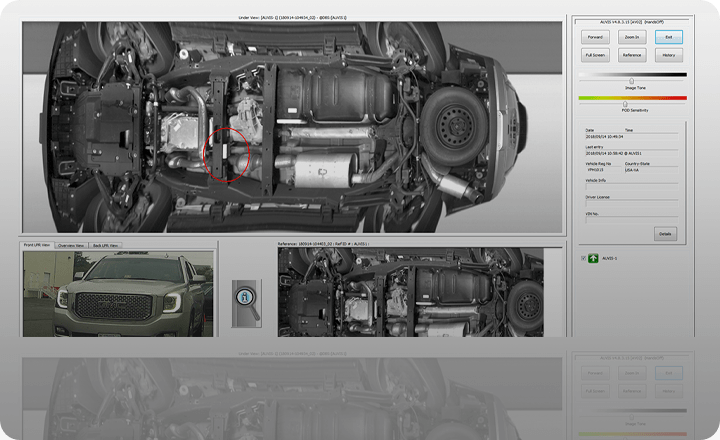
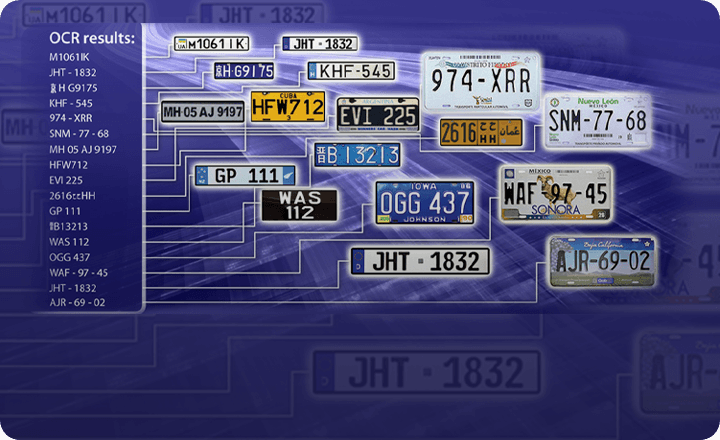
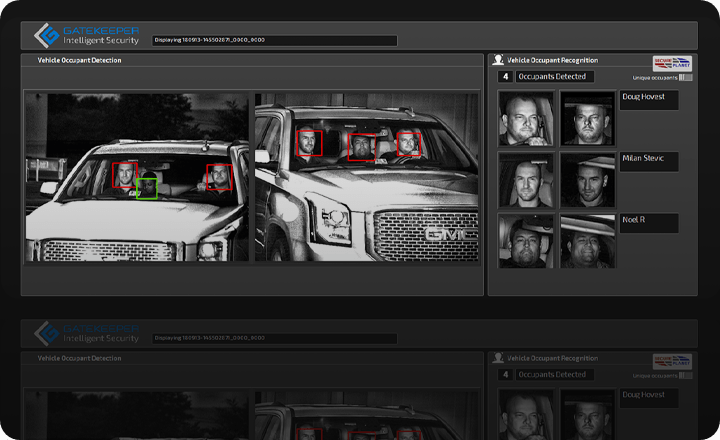
Perimeter
Security Solutions
Done-for-You!

At Concentric Security, we know your venue is unique. You have different security needs, challenges, stakeholders and technology requirements. This is where we shine.
As the industry leader in perimeter security, we’ve seen it all and know there is no one-size-fits-all solution.


Let’s Talk!
Contact us here and get a shortcut to the answers you need.
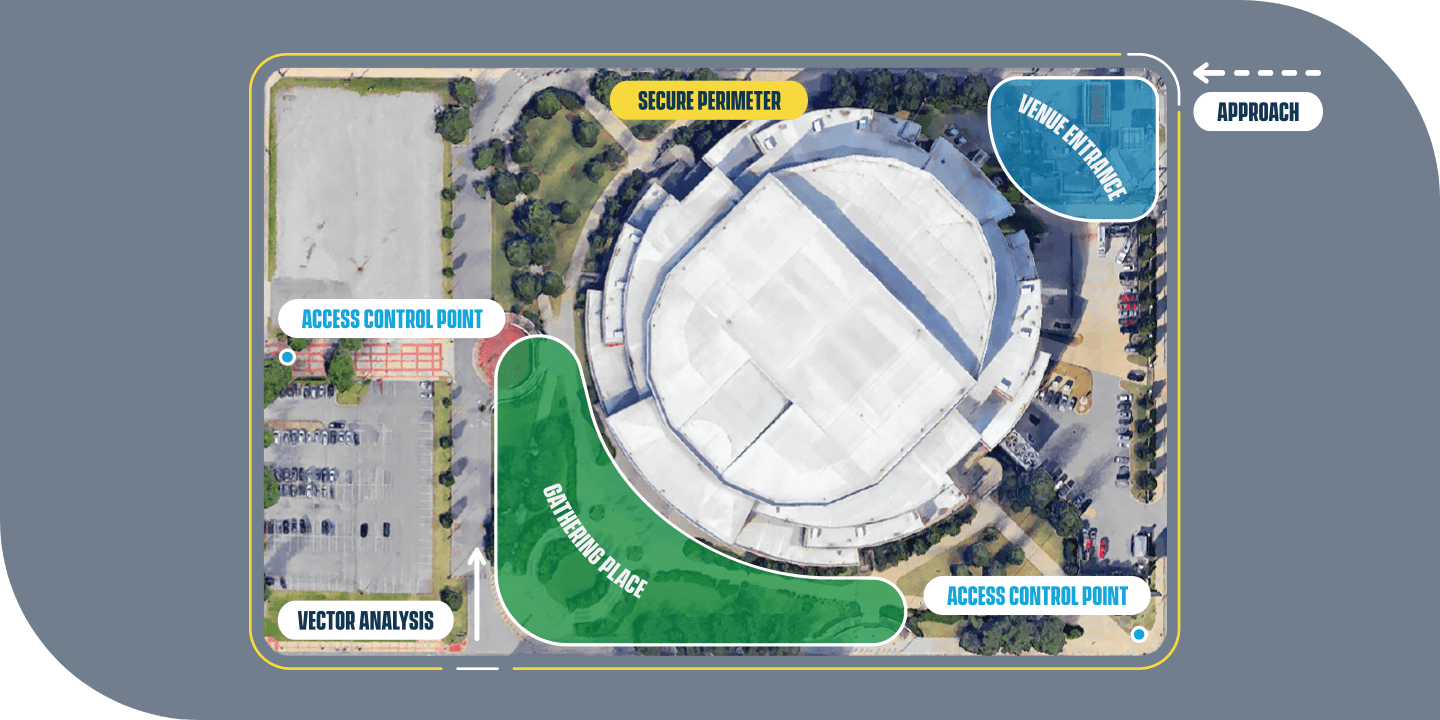
Assessment
- Site Characteristics
- Vulnerability Assessment
- Vector Analysis
- Blast Analysis
- Threat Verification
- Stakeholder Input
Engineering
- Technology Selection
- Civil Review
- Existing Infrastructure
- Underground Encumbrances
- Drainage
- Layout Design
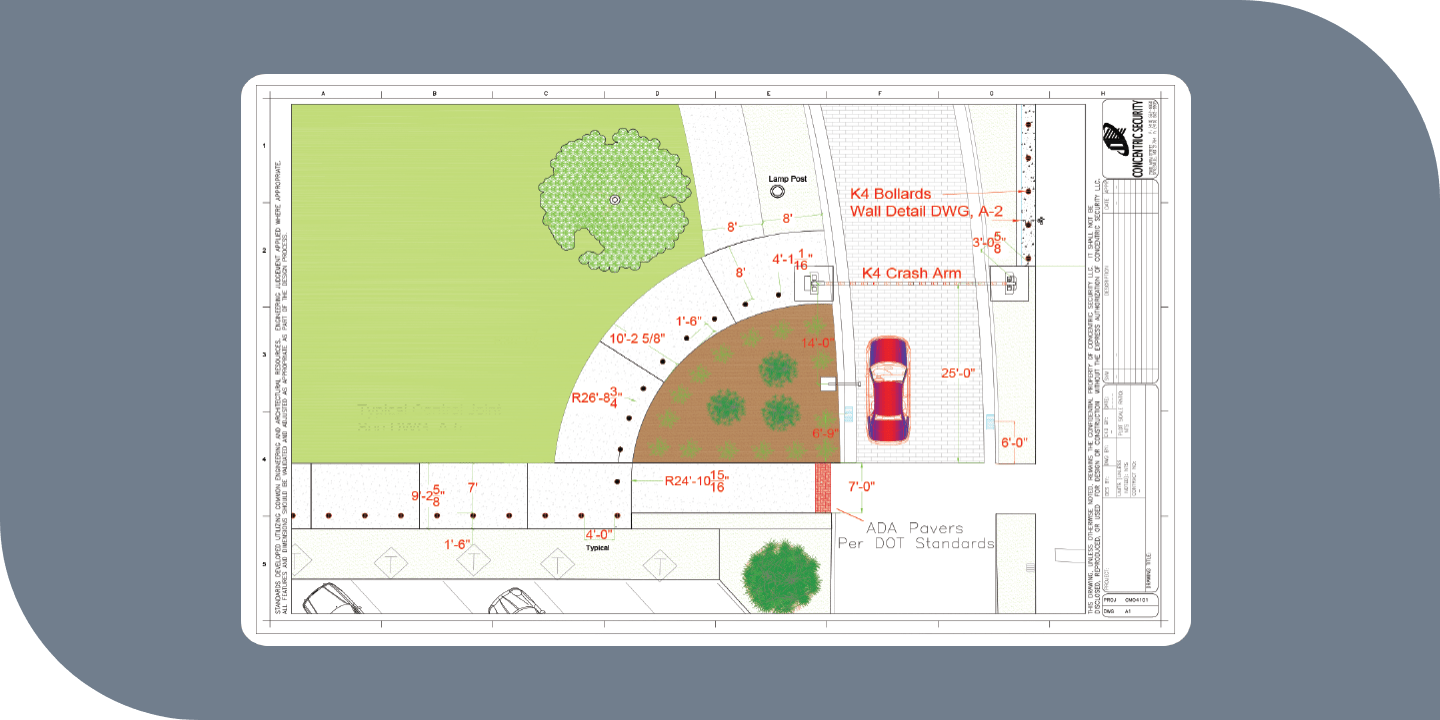
Construction
- Submittals
- Material Procurement
- Installation
- Verification Testing
- Training
- Warranty & Service

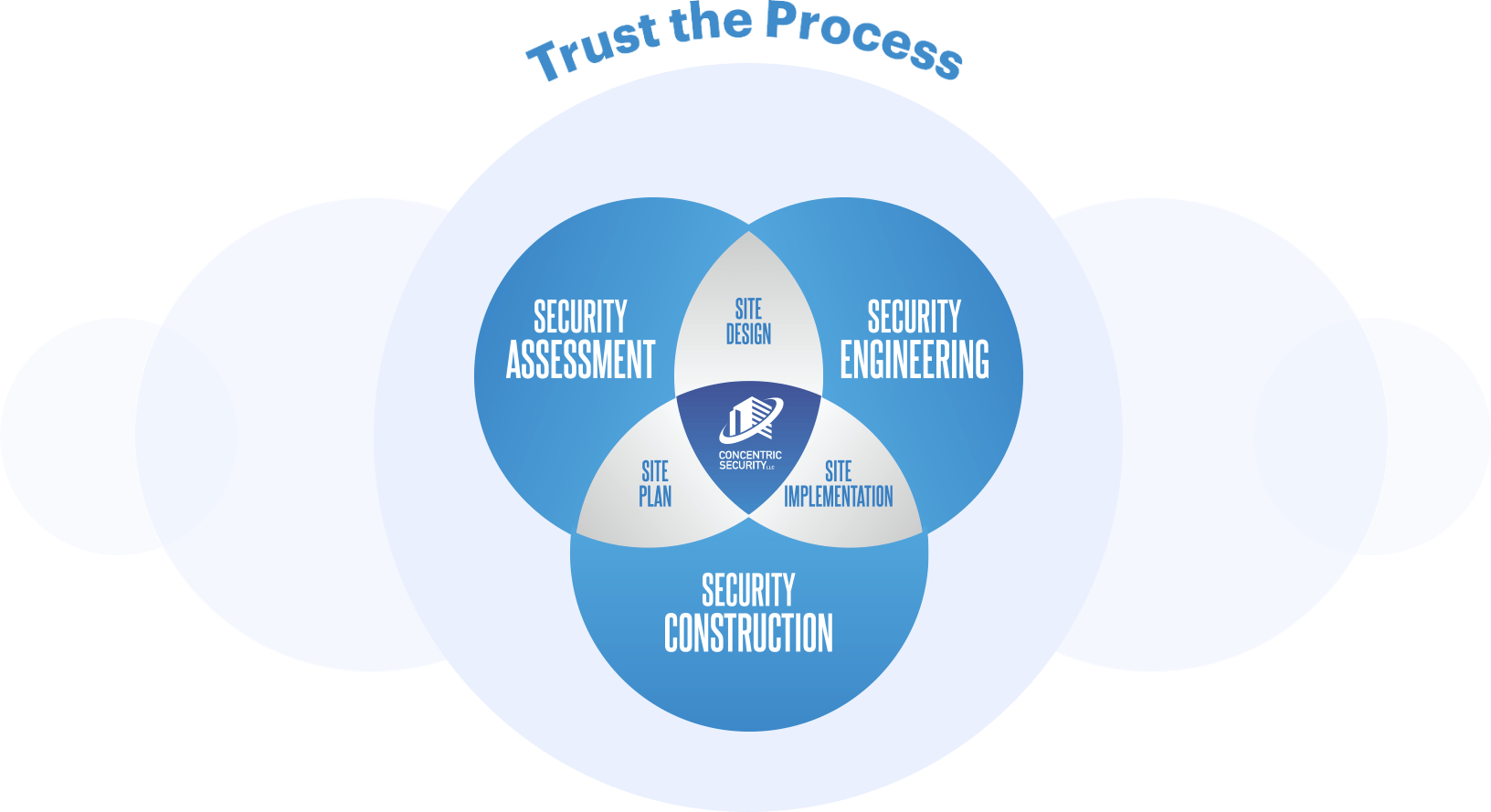
Learn more about how the Concentric Security Process can help you rest easy
and feel confident your guests are protected against vehicular attacks.
Unique
Perimeter Security Solutions



Shallow Mount Solutions
Perimeter Access Control