Perimeter Security
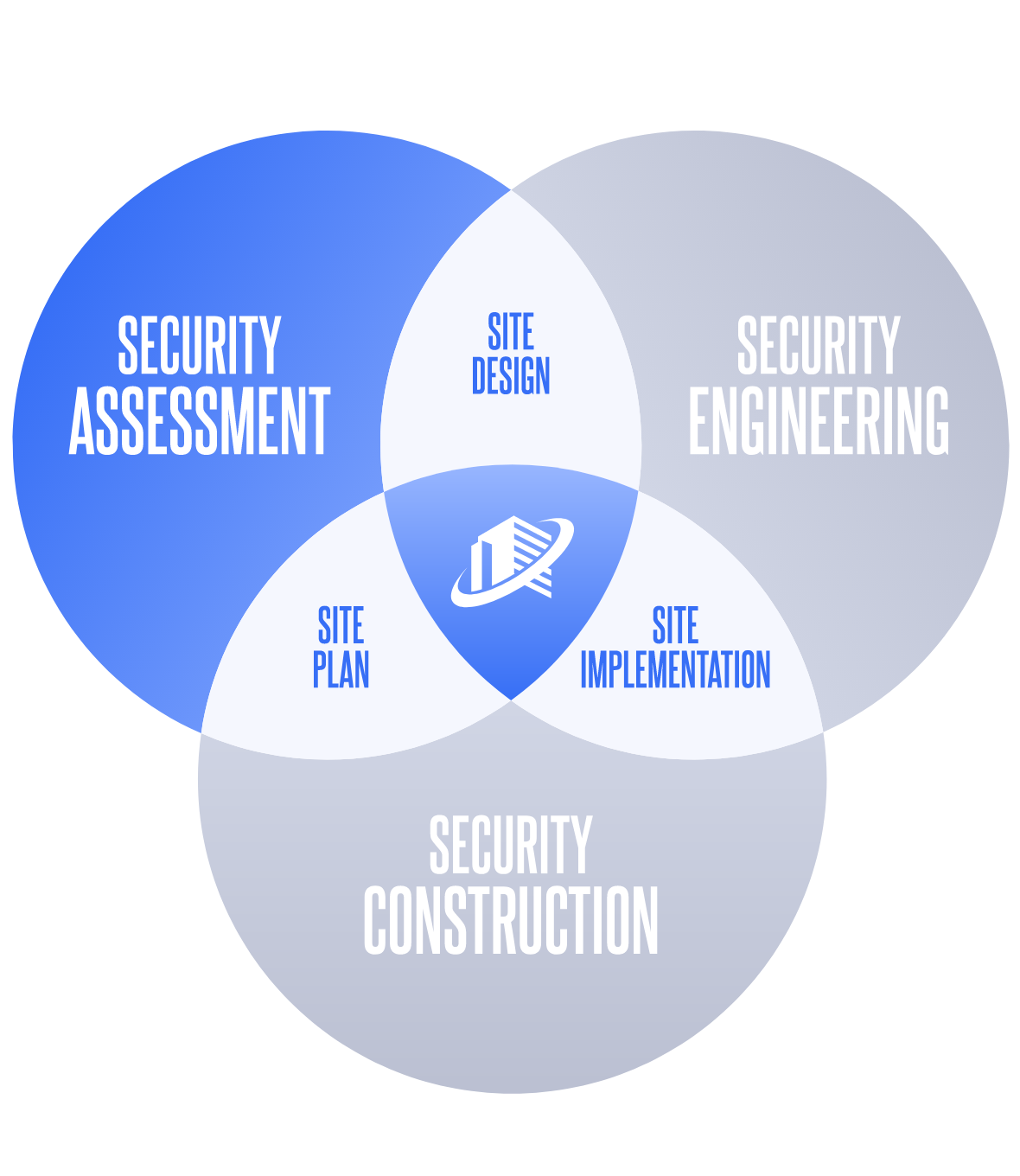
Solutions Process
Let’s get you to a solution:
Security Assessments
Our team knows every site and situation is different, there is no easy one size fits all answer. Knowing your site is the most important point when securing the perimeter of your facility from vehicle threats.
Strong security solution start with security assessments. Concentric Security works with you on a detailed analysis of your site and a practical plan.
Vulnerability Assessment
- Gathering Places
- Pedestrian Flow
- Determine Threat Scenarios (DBT)
Site Characteristics
- Property Layout/Boundaries
- Traffic Flow/Types
- Available Standoff Distances
- Facility Usage
- Stakeholder Constraints
Threat Verification
Stakeholder Input
Vector Analysis
- Review Possible Vectors
- Analyze Avenues of Approach
- Assess Roadway Geometry
Blast Analysis
- Blast Hazard Mitigation Review
- Standoff Distance Review








