Data Center Security
Advanced Physical Security in a Digital World
Are you constantly evaluating the security of your data center against vehicle-based threats?
Do you seek a comprehensive understanding of the potential costs without compromising on quality or expertise?
In response to the escalating cyberterrorism landscape and its implications for physical security, particularly in the realm of data centers, Concentric Security stands at the forefront of providing robust solutions against forced vehicle entry and perimeter vulnerabilities.
We understand the unique challenges that come with securing data center facilities, which are often hurried into deploying defenses that may result in costly and suboptimal outcomes. Our methodology is deeply rooted in Department of Defense best practices, ensuring that every implementation of vehicle barrier systems and perimeter security measures adheres to rigorous standards and specifications.
At Concentric Security, we pride ourselves on guiding our clients through the complexities of selecting and implementing the most appropriate security measures. Our approach is holistic, focusing on three essential areas:
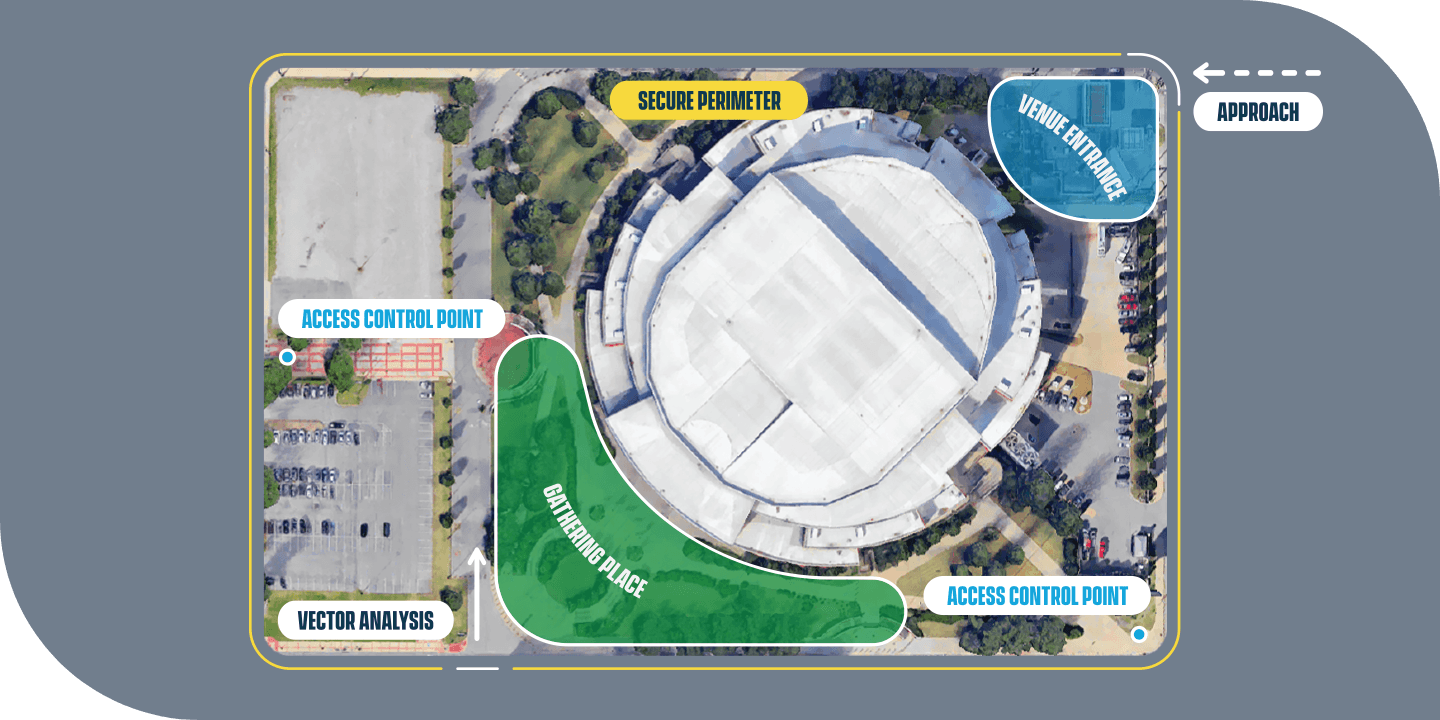
1. Site Perimeter
- Fencing - Crash rated fencing at least 20 feet from the building on all sides.
- Barriers - Each access point on the perimeter should have a human guard and physical barriers.
- Gates - For entry and exit of the site with photographic ID for employees / visitors.
- Signage - There should be no obvious identifier that the site is a Data Center externally.

.png)
2. Access Control Points
- Guard Booth - All entrances to the site should include a mantrap, physical barriers and CCTV cameras.
- S.M.A.R.T. Controls - A unique, innovative system monitor and reporting tool that improves the security, safety and system integrity of your vehicle barriers.
- Traffic Control - Only let approved vehicles enter or exit specific areas.
- Integration - Seamlessly integrate the access point technology with existing security infrastructure.
3. Facilities
- Turnstiles - Enhancing access control and preventing unauthorized entry into a secured perimeter.
- Mantraps - Mantraps offer a double-door security mechanism, requiring individuals to pass through a series of interlocking doors, ensuring a controlled and secure entry point to a facility's perimeter.
- Window Films - Provide blast mitigation capabilities, helping to prevent glass fragmentation during an explosion and reducing the risk of injury and damage to the building's interior.

Why Work with Us?
1. Our Proven Track Record of Excellence
At Concentric Security, we pride ourselves on our unparalleled proficiency and deep-seated experience in providing top-tier security solutions across various industries, with a special focus on Data Centers.
Our robust portfolio includes working closely with more than 25 Data Center Locations in the United States. Our dedication to excellence is evident in the testimonials we receive.
We understand the unique challenges and specific needs of the Data Center industry and are dedicated to delivering high-quality, customized security solutions that inspire confidence and peace of mind.
Trust us to bring you the best in the industry, because at Concentric Security, your security is our priority.


Concentric Security offers a wide variety of safety solutions and products.
Not sure which solutions suit you? We can help!
As the industry leader in Perimeter Security, we've seen it all and know there is no one-size-fits-all Solution. Concentric Security meets you where you want to be met.
We value your unique security needs, challenges and technology requirements and we offer you a proven process of Assessment, Engineering, Construction and Service to solve your security challenge in the best possible way.
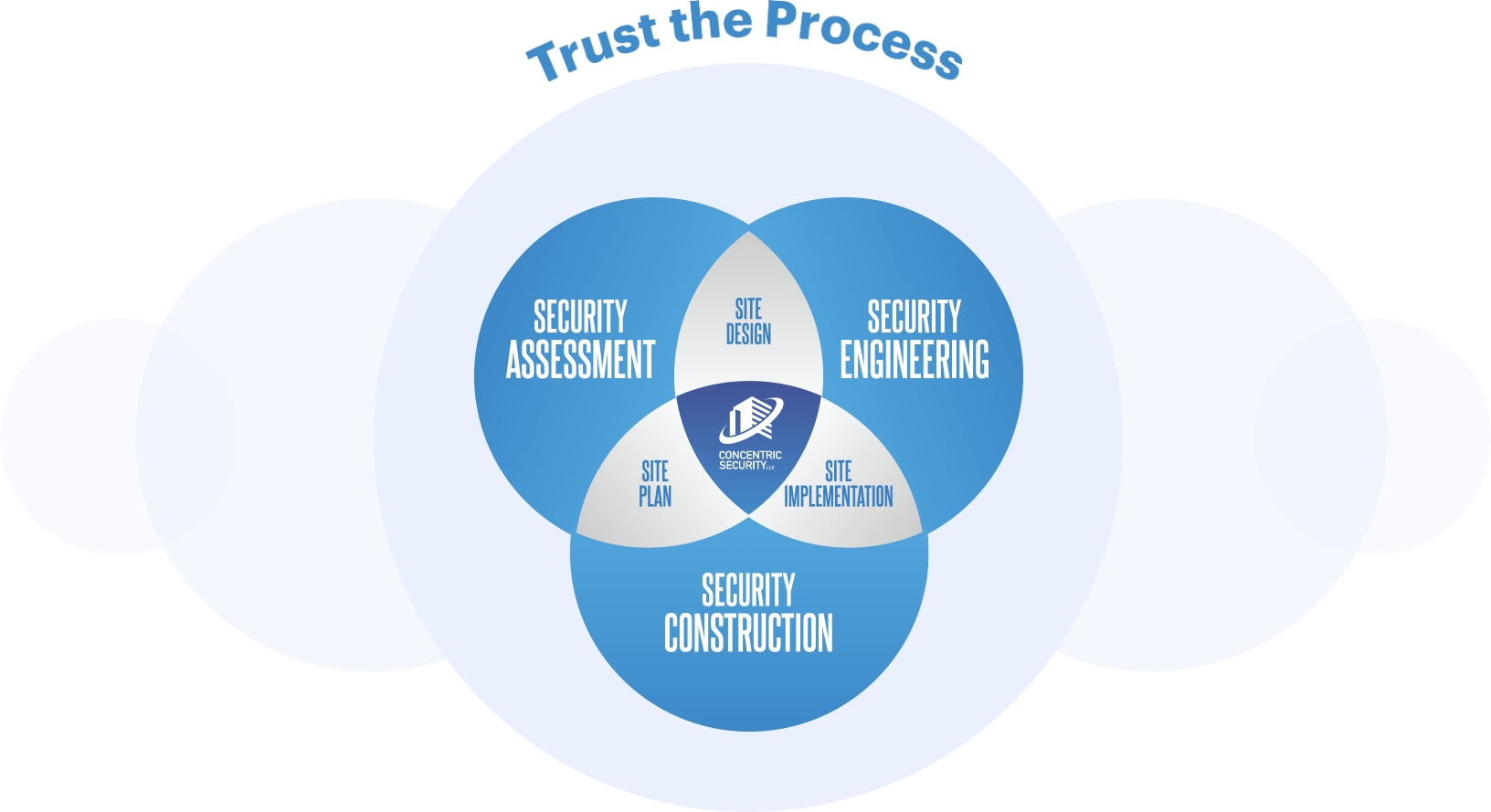
Assessment
-
Site Characteristics
-
Vulnerability Assessment
-
Vector Analysis
-
Blast Analysis
-
Threat Verification
-
Stakeholder Input
Engineering
-
Technology Selection
-
Civil Review
-
Existing Infrastructure
-
Underground Encumbrances
-
Drainage
-
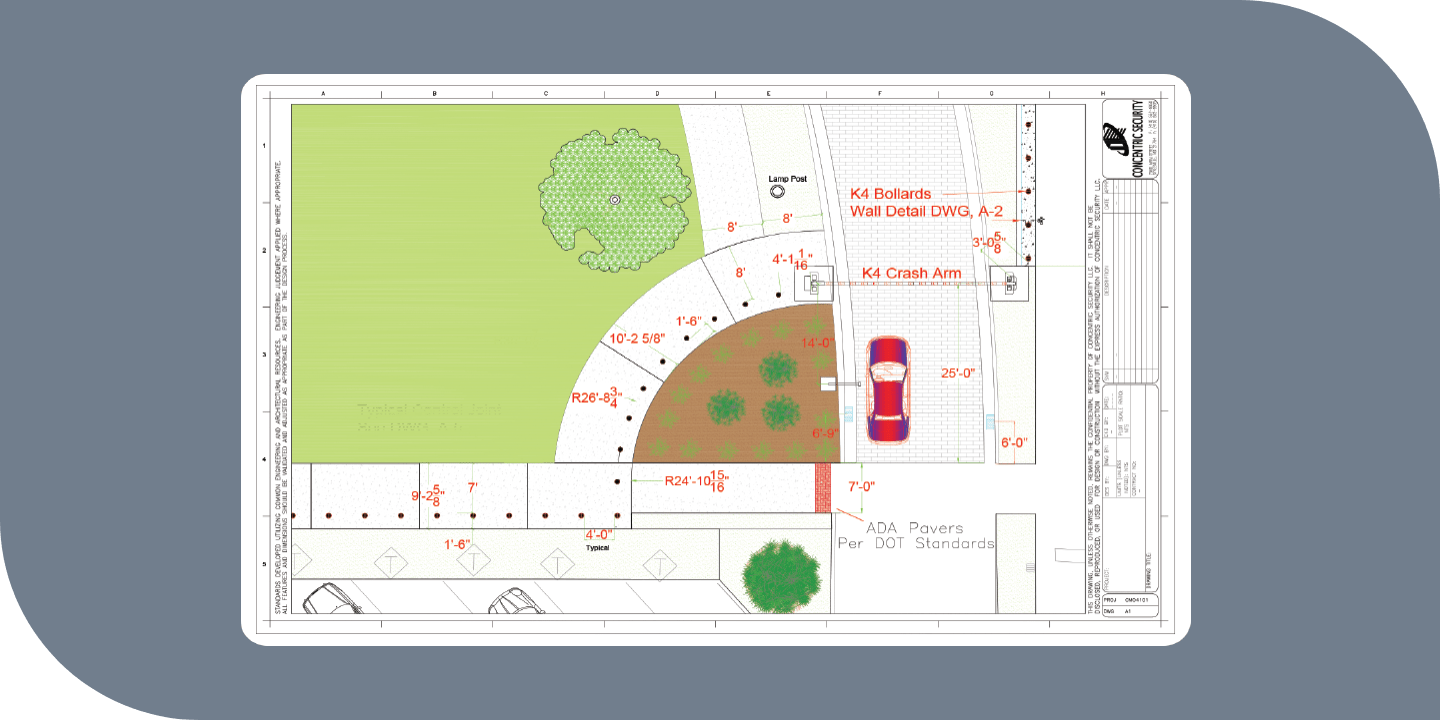
Layout Design
Construction
-
Submittals
-
Material Procurement
-
Installation
-
Verification Testing
-
Training
-
Warranty & Service


Service
-
Barriers of All Types
-
Controls
-
Minor Repairs
-
Preventative
-
Example
-
Services
3. Our People
Our Team
Concentric Security’s team is composed of seasoned veterans in the security industry that have been involved in both security design and construction. Our team consists of Physical Security Professionals (PSP), construction managers, design engineers, control engineers and professional engineers (PE). Our staff is dedicated to providing the best solution to fit the needs of our customers. The knowledge, integrity, execution and passion for service that our TEAM delivers are beyond compare.
Management
Concentric Security’s management has over 75 years of combined experience in all facets of the security design and construction. Our management team is dedicated to making Concentric Security the leading Perimeter Security Company in the nation by creating an atmosphere that challenges the staff to go beyond the customers’ expectations and provide the utmost in customer satisfaction.
Secure a Comprehensive Site Assessment with a Concentric Expert - At Zero Cost.
Our team of experts is more than happy to consult with you either virtually or in person as the situation dictates. We’ll assess general vulnerabilities and access points and provide guidance to possible solutions.
Should you find it more convenient, you can just give us a call at 410-552-9950.
Learn more about how the Concentric Security Process can help you rest easy and feel confident your data and employees are protected against attacks.

.png)







